CAN reversing with CANToolz
PHDays happened on May 17-18, in Moscow. It was a really great event and I believe PHDays is one of the best IT-Security event in Russia (but of course Zeronights is the best of the best). And during this event there was a small CAR/CAN-quest prepared by my friends and my small support (as CANToolz developer). Here I want to do a small write-up about it.
On first day of the conference we had "offline" task with real CAN dumps. Those who solved this task got access to the second level on second day of the conference. And this second task was based on a real vehicle that was parked inside main venue. But let's talk more detailed.
_Saplt, _j0hnni3 and @Z0ha4
---->
1st TASK
You have two DUMPS of CAN traffic: NOISE and EVENT, EVENT dump contains event of locking vehicle. Based on this two dumps please answer on following questions:
1) Which CAN frame (ID, DATA) allows to lock the car
2) Which CAN frames (ID) tell us about doors statues (find at least two)
3) What type of vehicle is it (vendor/)?
DUMPS:
NOISE - dump of the CAN traffic from the car for 1 minute. Engine turned on. No Actions
EVENT - dump of the CAN traffic from the car during lock event enabled. Engine turned on.
SOLUTION:
This task supposed to be simple and funny (fast filter to limit access to real vehicle on the second day only to those who really want to play). Let's start from first part of the task: how to find control frame which do a car-lock. Dump files have simple format: ID:LENGTH:DATA_IN_HEX so you can write a simple script to parse it or use CANToolz (this is format of REPLAY module of CANtoolz). First of all what we want: load DUMP files and replay it to mod_stat module for future analysis. For that we need simple config file (first_config.py):
This task supposed to be simple and funny (fast filter to limit access to real vehicle on the second day only to those who really want to play). Let's start from first part of the task: how to find control frame which do a car-lock. Dump files have simple format: ID:LENGTH:DATA_IN_HEX so you can write a simple script to parse it or use CANToolz (this is format of REPLAY module of CANtoolz). First of all what we want: load DUMP files and replay it to mod_stat module for future analysis. For that we need simple config file (first_config.py):
# Load modulesload_modules = { 'mod_stat' : {}, 'gen_replay' : {} } # Scenario actions = [ {'gen_replay' : {'pipe': 1}}, # REPLAY {'mod_stat' : {'pipe': 1}} # Analyze ]
Then just use web-browser: http://localhost:4444/index.html
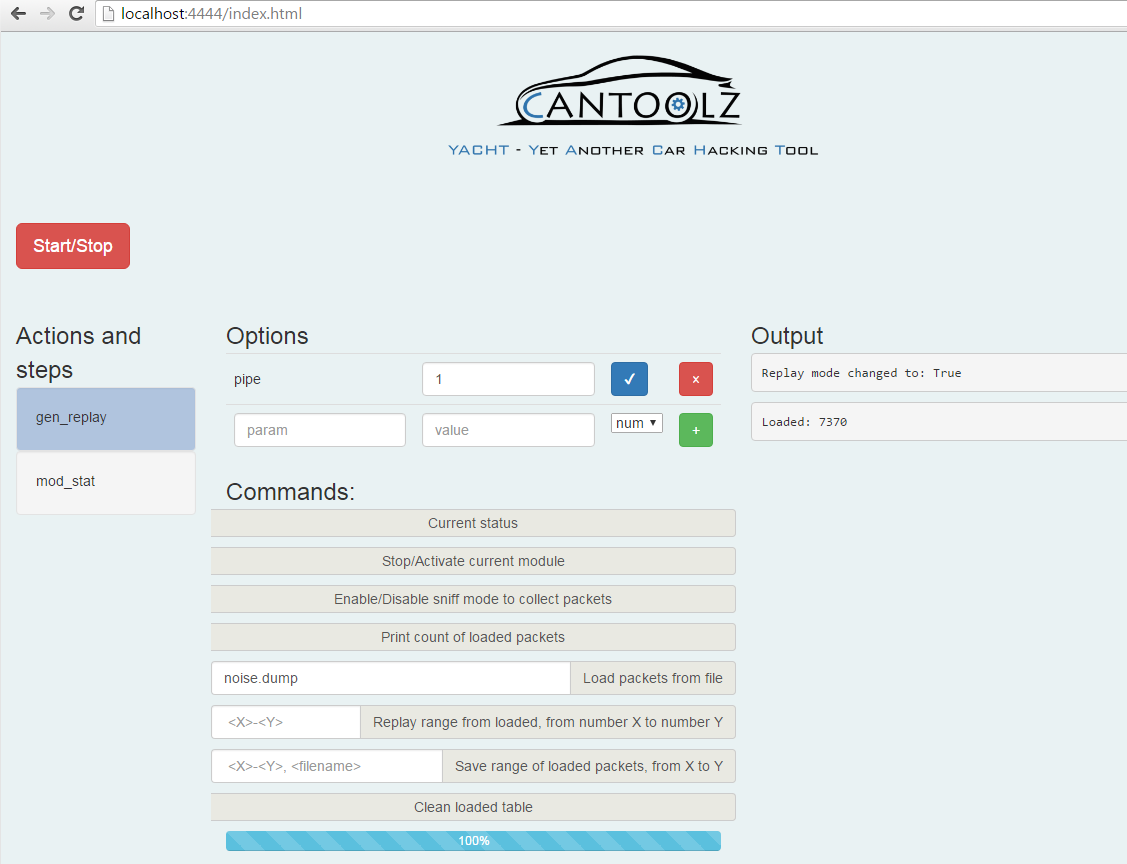
As result you will see CANToolz's web interface and two modules loaded: gen_replay and mod_stat.
Click on mod_replay and load noise dump. Then press START. Now you have noise dump loaded and ready for replay. If you click "replay" then all those frames will be replayed through CANToolz and will be sniffed by mod_stat (as a next module on the same PIPE).
Click on mod_replay and load noise dump. Then press START. Now you have noise dump loaded and ready for replay. If you click "replay" then all those frames will be replayed through CANToolz and will be sniffed by mod_stat (as a next module on the same PIPE).
Now we need to switch sniffing buffer in mod_stat to another index. For that click on mod_stat control, and then click "Switch sniffing to a new buffer". After that we can go back to gen_replay, clean it, load event.dump and replay it. As result in mod_stat we will have two buffers with replayed CAN traffic. In first buffer (index 0) we have noise dump, in second (index 1) we have event traffic. Now we can try to do a simple diff: Arbitration ID that exists in the second set but not in the first. In other words: which CAN frames are uniquely in second dump (by arbitration ID). For that diff. just press "Print Diff between two buffers (new ID only)".
With very high probability this is our answer on the first question of the task (0xef81296:2:0100). Why? Because this frame "fired" once during the event and have not been seen before (on real car, you can validate this by sending this command and check if car was really locked, but here on this test you can see that there are no other frames that looks like "command"). As you can see this is work of 3 minutes. So this is first part of our answer. But how to answer on the second question: Which CAN frames (ID) tell us about doors statues (find at least two)?
Idea with "status" frames also kind of simple. If we "0xef81296" control frame that changes status then it means, that just after this frame "statuses" of door should be changed. Then we could try to find this in the second buffer: check all messages before 0xef81296 and then after. If in those frames "after" event value has been changed: then it could be our "door statuses" data. This feature was not developed in CANToolz and not available during PHDays. So I am happy that at least one person (Dr.Glukyne) were able to understand this logic and develop a script to parse dump and find changes in the traffic after "control" frame have been sent. Right now this feature (as experimental) has been added into CANToolz 3.3.3, so no needs in manual scripting. But even without this feature in CANToolz you can get those "statuses" frames. The answer is in "Print Diff between two buffers". This time it was possible to do during PHDays via CANtoolz. Main idea in this scenario - that "statuses" frames are also exists in "noise" dump, and have been changed only in event dump (after "control" frame, but here this does not matter). We will do a diff between two buffers but not by Arbitration ID, but by CAN frame's data. For that we will put parameters: 0, 1, 2. (see screenshot below)
0 - Index of buffer for noise diff.
1 - Index of buffer for event diff
2 - filter: max count of different values. We set two, because we believe that in noise it was one value, and after "control" frame was sent it changed to another. So maximum we will have two different values.
0 - Index of buffer for noise diff.
1 - Index of buffer for event diff
2 - filter: max count of different values. We set two, because we believe that in noise it was one value, and after "control" frame was sent it changed to another. So maximum we will have two different values.
Also you can see that we check this with "Search ID in all buffers" and see exactly what have been changed in data. But as I told in version 3.3.3 I have implemented idea of Dr. Glukyne, let's check and compare results for both methods:
Yey! Both results are correlated and right (0x12f8... are the answers) ! Both methods works.
And I can say this is just a PoC. Right now another CANToolz developer - Sergey Kononenko is working on algorithms for correlation and "smart event detection" and we will present it on MOSEC conference on Jule 1 in Shanghai. It will be cool!
And I can say this is just a PoC. Right now another CANToolz developer - Sergey Kononenko is working on algorithms for correlation and "smart event detection" and we will present it on MOSEC conference on Jule 1 in Shanghai. It will be cool!
P.S. On last screenshot you see that after changes we have same values (0x80) again. this is bug in DUMP, since I cut it wrong 8( But anyway it did not affect hack-quest challenge.
Oh yeah... and last part: how to get carmaker and model? This is simplest thing. Just press "Analyses of captured traffic". And here CANToolz have re-assembled chain of few CAN frames, and detect ASCII. This ASCII will be a VIN number which you can google and find who is a vendor and what model it was (of course this VIN is dumb-faked...).
As you see CANToolz can be very helpful and here a lot of features and methods that can help to understand whats going on in CAN bus! Yes... here we have kind of difficult interface and not-well-documented details... but have u seen Radare2? Just silly 8))) Promise to work on the documentation and hope for your feedback and etc.
TO BE CONTINUED ...




Hi All!
ОтветитьУдалитьI'm selling fresh & genuine SSN Leads, with good connectivity. All data properly checked & verified.
Headers in Leads:
First Name | Last Name | SSN | Dob | Address | State | City | Zip | Phone Number | Account Number | Bank Name | DL Number | Routing Number | IP Address | Reference | Email | Rental/Owner |
*You can ask for sample before any deal
*Each lead will be cost $1
*Premium Lead will be cost $5
*If anyone wants in bulk I will negotiate
*Sampling is just for serious buyers
Hope for the long term deal
For detailed information please contact me on:
Whatsapp > +923172721122
email > leads.sellers1212@gmail.com
telegram > @leadsupplier
ICQ > 752822040
why my canon printer is printing blank pages
ОтветитьУдалитьwhy does my canon printer print blank pages
canon printer printing blank pages
microsoft word not responding
microsoft word keeps crashing mac